Strengthening Your Web Apps: A Guide to HTTP Security Headers
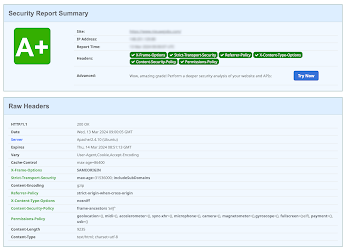
There is a certain set of standard HTTP headers that every website should ideally set to provide a basic level of security. This note discusses such headers and how to set them on sites deployed in Netlify. Common security headers First, let’s consider basic HTTP headers - they are common to all requests and provide a basic level of security. The Content-Security-Policy header helps protect your website from cross-site scripting attacks by providing a list of approved content. This header allows you to prohibit the use of content that does not pass the rules or should not be used as content. Setting this header may seem complicated, so if you want to delve into the topic, visit the official website. Example usage: Content-Security-Policy: default-src 'https://example.com'; script-src 'unsafe-inline' 'https://example.com'; style-src 'unsafe-inline' 'https://example.com'; object-src 'none' The X-Frame-Options header tells the brow...